Because I use WordPress to host this site, I also use a well-known WordPress security plugin called wordfence. If you have a wordpress site, you probably should look into ramping up your security with wordfence or similar. I have the free version, and no this is not an ad. The price for having their free version is that I am on their mailing list, and as a result I get weekly security related emails and also alerts if a new wordpress hack has been discovered.
Because I use WordPress to host this site, I also use a well-known WordPress security plugin called wordfence. If you have a wordpress site, you probably should look into ramping up your security with wordfence or similar. I have the free version, and no this is not an ad. The price for having their free version is that I am on their mailing list, and as a result I get weekly security related emails and also alerts if a new wordpress hack has been discovered.
Now here comes the interesting part, the Russian hacking claim is within their remit and so they have issued their analysis of the available evidence.
So here is where things stand.
The US Department of Homeland Security (DHS) and the Office of the Director of National Intelligence (DNI) released a Joint Analysis Report, or JAR, compiled by the DHS and FBI. This is claimed to contain evidence of the election security compromises by Russian intelligence operatives.
So what exactly did the Wordfence analysis of this report reveal?
Their analysis of it all is here …
US Govt Data Shows Russia Used Outdated Ukrainian PHP Malware
Warning, it is long … very long, so here are a few key conclusions.
Malware Sample
DHS and DNI have released a joint statement that says:
“This document provides technical details regarding the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. Government, political, and private sector entities. The report contains specific indicators of compromise, including IP addresses and a PHP malware sample.”
The PHP malware sample they have provided appears to be P.A.S. version 3.1.0 which is commonly available and the website that claims to have authored it says they are Ukrainian. It is also several versions behind the most current version of P.A.S which is 4.1.1b. One might reasonably expect Russian intelligence operatives to develop their own tools or at least use current malicious tools from outside sources.
Analysis of the IP addresses provided by DHS and DNI
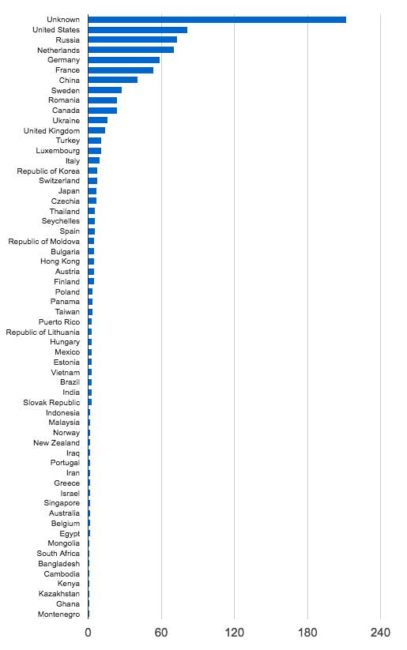
DHS provided us with 876 IP addresses as part of the package of indicators of compromise. Lets look at where they are located. The chart below shows the distribution of IP addresses by country.
…What we’re seeing in this IP data is a wide range of countries and hosting providers. 15% of the IP addresses are Tor exit nodes. These exit nodes are used by anyone who wants to be anonymous online, including malicious actors.
There is also a new updated FAQ on it all
Their initial analysis received rather a lot of attention, and so they now have a FAQ to help clarify a few key points …
Our business is WordPress security and our customers use WordPress and the Wordfence firewall and malware scanner. Some of this report will be talking directly to our customers, and some of it will be helpful for those interested in security in general and global events.
But perhaps the most important point there is this …
Does the report prove that Russia Hacked the 2016 US Election?
No it does not.
Further Thoughts
What is the truth here?
We are dealing with the intelligence community so I would not expect them to place the precise details of what they actually know on the table.
What can we actually conclude?
There are various possibilities …
- The US Intelligence community is rather incompetent and actually believes that this outdated Ukrainian malware is “evidence” of Russian hacking
- The US Intelligence community is playing a long game here and wants to mislead other game players into thinking that they are inept and incompetent.
Personally I’d be placing my money on the latter. Even Wordfence who are just a small business, do not publicise all their firewall rules. As for how secret the intelligence community is, we all know that the Enigma code was cracked in 1940s, but that was kept secret until the 1970s and the full details never emerged until the 1990s. Secrecy is how this closed-loop community functions.
Of Related Interest
- Glenn Greenwald lays out a robust case that the “Russian Hacking of the US Electricity Grid” is a bit of hysterical nonsense and not at all factual.
- A retired CIA operations officer explains why they will never ever reveal what they actually know and how they know it.
Final Hat Tip to Wordfence
When reviewing logs yesterday, I noted several Ukrainian IP addresses have been attempting to hack in by attempting to guess passwords. I’m not claiming to be in any way special, I suspect almost every single wordpress install they can find will be sniffed like this.
- Thanks to wordfence three or more attempts to login were automatically blocked
- I’ve now permanently blocked the originating IP addresses.
Over time you become familiar with specific patterns …
- Rather a lot of attempts to break in come from Ukrainian sources
- Rather a lot of fake comments that are really links to ads come from China.
The Chinese spam bots are better at using vast swathes of dynamic IP addresses, so I’m forced to block entire ranges.
So yes, this all sounds like an ad for the folks behind the plugin, but hey, they have saved my bacon, hence from my viewpoint they earned a hat tip from me.